Have you ever noticed that green padlock in your browser’s address bar? Or Why some fishy websites show a “Not Secure” warning?
Well, this about HTTPS – the security protocol that has become the backbone of safe internet communication.
Imagine sending your data in a sealed envelope versus a postcard that anyone can read. Nowadays cyber attacks methods keep evolving and are very sophisticated.
HTTPS too has equally evolved from being a nice-to-have feature to an absolute necessity for every website or web application.
What is HTTPS?
The Basics
HTTPS stands for Hypertext Transfer Protocol Secure, and it’s the secure version of HTTP – the protocol that powers the World Wide Web.
Think of HTTP as the language browsers and servers use to communicate, while HTTPS is that same language but with a encryption layer wrapped around it.
HTTP transmits data in plain text, making it readable to anyone who intercepts it, while HTTPS encrypts all communication, turning readable information into gibberish code that only the intended recipient can decode and understand.
HTTP vs HTTPS data security comparison
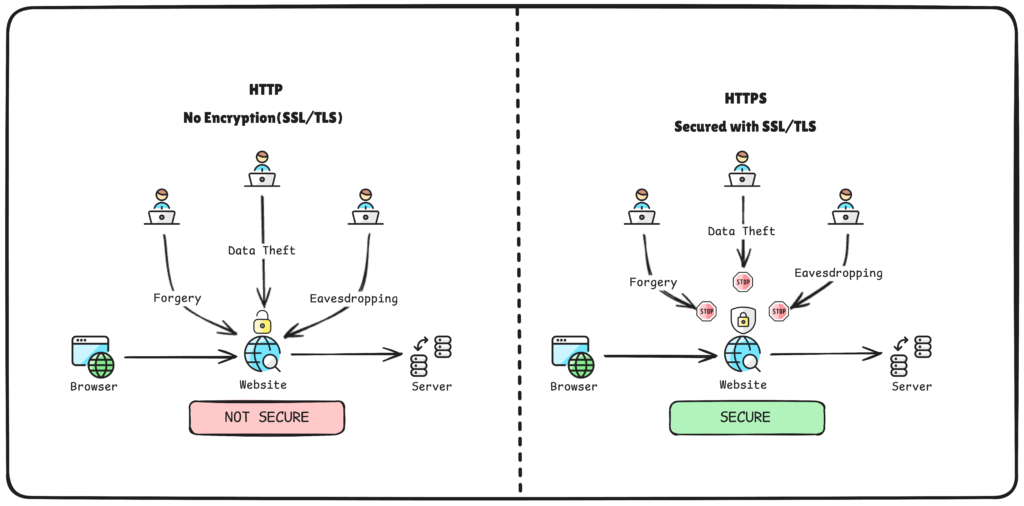
Three Pillars of HTTPS Security
HTTPS provides three critical security features:
1. Encryption (Confidentiality)
All data transmitted between your browser and the website is encrypted using advanced algorithms. If someone intercepts the communication, they’ll see nothing but random characters.
2. Authentication
HTTPS ensures you’re actually communicating with the website you intended to visit, not an dummy fraud website. This is achieved through digital certificates issued by various trusted Certificate Authorities (CAs).
3. Data Integrity
The protocol guarantees that the information remains untampered during transmission. If someone tries to modify the data, HTTPS will detect it immediately.
Deep Dive To The Technical Foundation
The Role of SSL/TLS Protocols
HTTPS relies on Transport Layer Security (TLS), which is the modern successor to Secure Sockets Layer (SSL). While these terms are often used interchangeably, TLS is the current standard that actually works behind HTTPSsecurity.
The protocol uses a sophisticated combination of symmetric and asymmetric encryption:
- Asymmetric encryption (public key cryptography) is used during the initial handshake to securely exchange keys.
- Symmetric encryption is then used for the actual data transmission, as it’s much faster for large amounts of data.
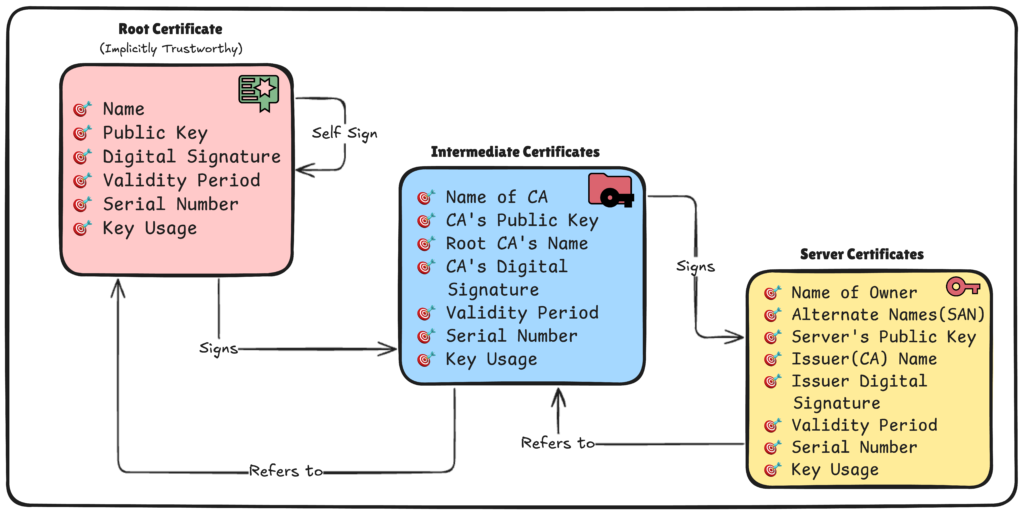
The Public Key Infrastructure (PKI)
The core of HTTPS lies Public Key Infrastructure (PKI), a framework that manages digital certificates and encryption keys. PKI involves several key players:
- Certificate Authority (CA): A trusted organization that issues and validates digital certificates.
- Registration Authority (RA): Processes certificate requests and validates applicant information.
- Digital Certificates: Electronic documents that bind public keys to their owners’ identities.
PKI certificate chain of trust structure
The HTTPS Handshake Process: Step by StepThe SSL/TLS handshake is a very important process that establishes a secure connection between your browser and a website. Let’s break down exactly what happens:
HTTPS SSL/TLS handshake process flow diagram
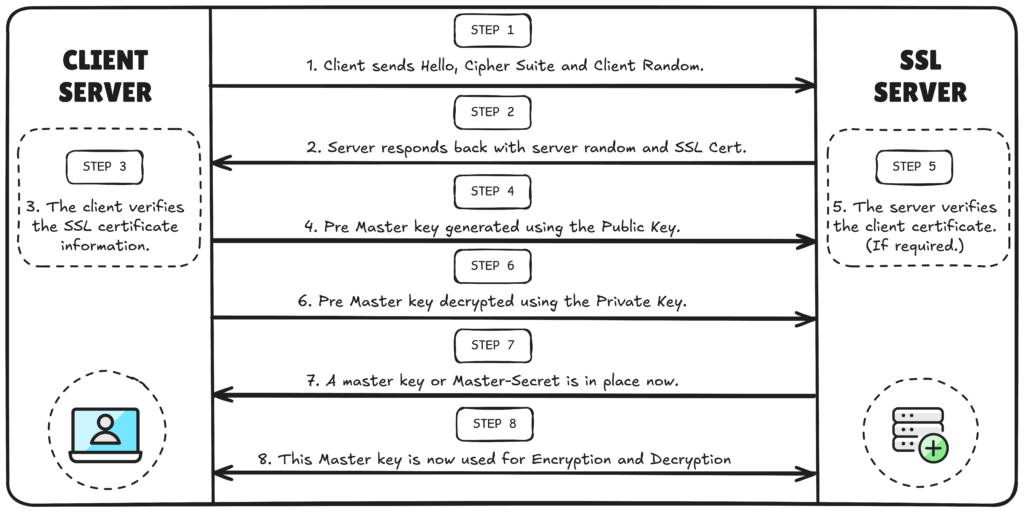
Phase 1: Client Hello
When you type “https://” into your browser, it sends a ClientHello message to the server containing:
- Supported TLS versions.
- Available cipher suites (encryption methods).
- A random number for cryptographic purposes.
- Session information.
Phase 2: Server Response
The server responds with a ServerHello message that includes:
- The chosen TLS version and cipher suite.
- Its digital certificate containing the public key.
- Another random number.
- Session ID.
Phase 3: Certificate Verification
Your browser performs several critical checks:
- Verifies the certificate hasn’t expired.
- Confirms it was issued by a trusted Certificate Authority.
- Ensures the domain name matches the certificate.
- Checks that the certificate hasn’t been revoked or tampered.
Phase 4: Key Exchange
If the certificate is valid, the browser:
- Generates a Pre-Master Secret.
- Encrypts it with the server’s public key.
- Sends it to the server.
Phase 5: Session Key Creation
Both the client and server use the exchanged information to create identical session keys for symmetric encryption.
Phase 6: Secure Communication Begins
From this point forward, all communication is encrypted using the shared session keys.
Examples and Commands
Checking HTTPS Certificate Information
Some useful terminal commands for inspecting HTTPS certificates:
Using OpenSSL to view certificate details:
openssl s_client -showcerts -connect example.com:443
| Command/Option | Explanation |
|---|---|
openssl | This is the command-line tool for using the OpenSSL library, which provides various cryptographic functions. |
s_client | This option specifies that you want to use the SSL/TLS client functionality to connect to a server. |
-showcerts | This flag tells OpenSSL to display the entire certificate chain sent by the server during the SSL/TLS handshake. |
-connect | This option is used to specify the server and port to connect to. |
example.com:443 | This is the target server (in this case, example.com) and the port number (443), which is the standard port for HTTPS connections. |
Using curl to test HTTPS connections:
curl -vvI <https://example.com>
| Command/Option | Explanation |
|---|---|
curl | This is a command-line tool used for transferring data with URLs, supporting various protocols including HTTP and HTTPS. |
-vv | This option enables verbose output, providing detailed information about the request and response, including headers and connection details. The -v flag can be used once for basic verbosity, and using it twice (-vv) increases the level of detail. |
-I | This flag tells curl to fetch only the HTTP headers of the response, rather than the full content of the page. This is useful for checking server responses without downloading the entire page. |
https://example.com | This is the target URL you want to connect to, using the HTTPS protocol. Replace example.com with the actual domain you wish to query. |
Using nmap to scan SSL certificates:
nmap -p 443 --script ssl-cert example.com
| Command/Option | Explanation |
|---|---|
nmap | This is a network scanning tool used to discover hosts and services on a computer network. It can be used for security auditing and network inventory. |
-p 443 | This option specifies the port to scan. In this case, it is port 443, which is the standard port for HTTPS traffic. |
--script ssl-cert | This flag tells Nmap to use the ssl-cert script, which retrieves and displays the SSL/TLS certificate information from the specified port. |
example.com | This is the target domain you want to scan. Replace example.com with the actual domain you wish to query. |
Generating SSL Certificates
Creating a self-signed certificate for testing:
# Generate private key
openssl genrsa -des3 -out server.key 4096
# Create certificate signing request
openssl req -new -key server.key -out server.csr
# Generate self-signed certificate
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
| Command/Option | Explanation |
|---|---|
openssl genrsa | Command to generate an RSA private key. |
-des3 | Encrypts the private key using Triple DES. |
-out server.key | Specifies the output file for the private key. |
4096 | Specifies the size of the key in bits (4096 bits). |
openssl req | Command to create a certificate signing request (CSR). |
-new | Indicates that a new CSR is being created. |
-key server.key | Specifies the private key to use for the CSR. |
-out server.csr | Specifies the output file for the CSR. |
openssl x509 | Command to create or manipulate X.509 certificates. |
-req | Indicates that the input is a CSR. |
-days 365 | Specifies the validity period of the certificate in days (365 days). |
-in server.csr | Specifies the input file for the CSR. |
-signkey server.key | Specifies the private key to sign the certificate. |
-out server.crt | Specifies the output file for the self-signed certificate. |
Testing HTTPS Implementation
Verify certificate installation:
# Check certificate expiration
openssl x509 -in certificate.crt -text -noout
# Test SSL configuration
curl -I <https://yourdomain.com>
| Command/Option | Explanation |
|---|---|
openssl x509 | Command to display or manipulate X.509 certificates. |
-in certificate.crt | Specifies the input file for the certificate to check. |
-text | Outputs the certificate in a human-readable format. |
-noout | Prevents the output of the encoded version of the certificate. |
curl -I | Command to fetch HTTP headers from a URL. |
https://yourdomain.com | The URL to test the SSL configuration for the specified domain. |
HTTPS Benefits and Importance
Security Advantages
- Protection Against Man-in-the-Middle Attacks: HTTPS prevents attackers from intercepting and reading your data when using public Wi-Fi or unsecured networks.
- Prevention of Data Tampering: The protocol makes sure that malicious parties cannot modify the information being transmitted.
- Authentication Assurance: Digital certificates guarantee you’re connecting to the legitimate website, not a fraudulent similar looking website.
Business and SEO Benefits
- Search Engine Rankings: Google considers HTTPS as a ranking signal, giving secure websites a extra points in search results.
- User Trust and Credibility: Browsers display visual indicators (padlock icon) for HTTPS sites, while flagging HTTP sites as “Not Secure”.
- Compliance Requirements: Many regulations, including GDPR, require adequate security measures, making HTTPS essential for legal compliance.
- Modern Web Features: Many new browser features and APIs require HTTPS to function, making it necessary for progressive web applications.
Essential Security Practices
1. Use TLS Everywhere: Implement HTTPS across your entire website, not just on login or checkout pages.
2. Enable HTTP Strict Transport Security (HSTS): Configure your server to send HSTS headers, forcing browsers to always use HTTPS.
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
| Command/Option | Explanation |
|---|---|
Header always set | Directive to set a specific HTTP header in the server response. |
Strict-Transport-Security | The name of the HTTP header that enforces HTTP Strict Transport Security (HSTS). |
"max-age=31536000; includeSubDomains" | The value of the header, where max-age=31536000 specifies that the browser should only access the site using HTTPS for the next 31536000 seconds (1 year), and includeSubDomains applies this rule to all subdomains. |
3. Implement Perfect Forward Secrecy: Enable PFS to ensure that even if your private key is compromised in the future, past communications remain secure.
4. Use Strong Cipher Suites: Configure your server to support only modern, secure encryption algorithms.
5. Keep Certificates Updated: Regularly monitor certificate expiration dates and renew them before they expire.
Certificate Management
Choose the Right Certificate Type:
- Domain Validation (DV): Basic encryption for simple websites
- Organization Validation (OV): Additional identity verification for businesses
- Extended Validation (EV): Highest level of validation for e-commerce sites
Proper Installation Process
- Generate a Certificate Signing Request (CSR)
- Submit it to a trusted Certificate Authority
- Complete domain/organization validation
- Install the certificate and intermediate certificates
- Test the installation thoroughly
Common Use Cases and Applications
- E-commerce and Financial Services: HTTPS is absolutely critical for any website handling payment information, personal data, or financial transactions.
- Content Management and Blogs: Even simple websites benefit from HTTPS as it protects user privacy and improves search rankings.
- API Security: RESTful APIs and web services should always use HTTPS to protect data in transit.
- Internal Corporate Applications: Private company websites and intranets should implement HTTPS to prevent corporate espionage.
Troubleshooting Common HTTPS IssuesCertificate Chain Problems
- Incomplete Certificate Chain: This occurs when intermediate certificates aren’t properly installed.Solution: Ensure all intermediate certificates are included in your server configuration.
- Mixed Content Warnings:Problem: Loading HTTP resources on an HTTPS page triggers browser warnings.Solution: Update all internal links, scripts, and resources to use HTTPS.
- Certificate Expiration:Prevention: Set up monitoring to alert you before certificates expire.
# Check certificate expiration openssl x509 -in cert.pem -text -noout | grep "Not After"Command/OptionExplanationopenssl x509Command to display or manipulate X.509 certificates.-in cert.pemSpecifies the input file for the certificate to check (in this case,cert.pem).-textOutputs the certificate in a human-readable format.-nooutPrevents the output of the encoded version of the certificate.“grep "Not After"Filters the output to show only the line containing “Not After,” which indicates the expiration date of the certificate.
Final Thoughts
Every website on the world wide web benefits from HTTPS, and is an essential standard. HTTPS simplifies the construction of communication networks that defend the website owners and end users from a host of cyber attacks.
It is equally important in improving search engine rankings. The presence of HTTPS is a must, is supported by all the web browsers.
HTTPS is fundamental in cyber security and remains the first shield in the line of attacks. Yet, cyber attacks remain persistent to evolve. his is where the recommendations of the guide in addition to ongoing recommendations come in the to help protect the privacy and the web communication.
Additional Resources
OWASP Transport Layer Protection Cheat Sheet – Comprehensive security guidelines for TLS implementation
- SSL Labs SSL Test – Free tool to test and grade your HTTPS configuration
- Mozilla SSL Configuration Generator – Generate secure SSL/TLS configurations for various web servers
- Let’s Encrypt – Free, automated certificate authority providing SSL/TLS certificates
- NIST Special Publication 800-52 – Government guidelines for TLS implementation
These resources provide detailed technical specifications, configuration examples and security best practices that will help you maintain secure and compliant web applications.


